I have upgraded cloud key with UDMPro. UDMPro don’t have a DNS. I plan to use Cloud Key as DNS and wanted to install PI-HOLE on it.
Followed these steps.
a) Factory Restore Cloud Key Power off the system.
b) Press and hold the reset button and then power on the Cloud Key by connecting it to the power source.
- Keep the reset button pressed for about 10 seconds, or until you see the recovery LED pattern in a loop (blue – off – white). The LCD screen on the front panel will also read “RECOVERY MODE.”
- Once the LED is flashing in the recovery mode pattern, open your browser and type the IP address for the Cloud Key, visible on the device’s screen. The IP address comes from your DHCP server, if you can’t access DHCP, the fallback IP will work: 192.168.1.30. However, keep in mind that if your Cloud Key does have a IP address assigned by the DHCP server, the fallback IP will not work.
- You should be taken to the Recovery Mode screen. From here you can reset, reboot, power off and most importantly you can upload an updated firmware bin file.
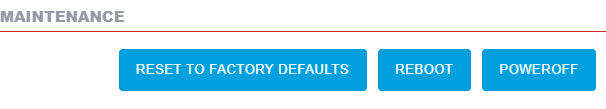
Click ton Reset to Factory Defaults and then Reboot. It would take 2-3 minutes to come back with a steady white light. You would see information on the LCD that its ready to be configured.
You can see the latest firmware by clicking here.
2) Open your browser and type the IP address for the Cloud Key, Disable update/diagnostic in wizard
Let it set up. After update, I can see UniFi OS Version2.3.10 on Cloud Key.
Uninstall All applications, Settings -> Update. There are three dots on the right of application icon, click and uninstall.
Enable SSHS by going into Settings -> Advanced and SSH.
Open Putty and SSH into Cloud key;
User = ubnt
Password = your password
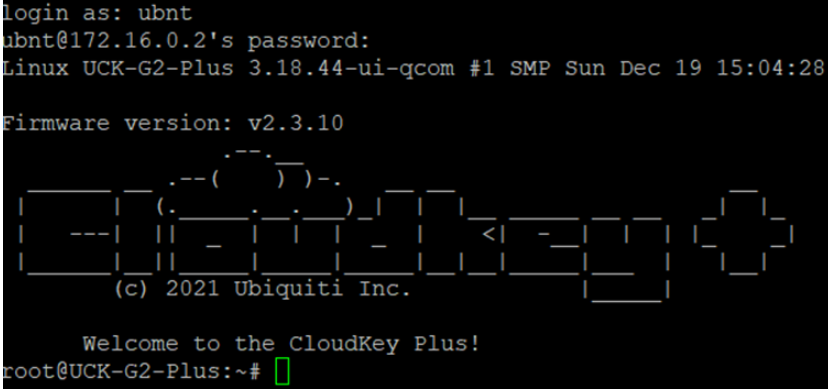
We are in console. If for some strange reasons, Web URL doesn’t work but SSH works, then cloud key can be reset to factory defaults by running this command;
/sbin/ubnt-systool reset2defaultsIt’s time to re-purpose cloud key. I have found this sequence on unifi forum. Follow step by step;
#go superuser
sudo –i
#Let’s install nano to make conf edit easier
apt-get install nano
#Install dnsmasq
apt-get update
apt-get install dnsmasq
#(Answer Y to replace the files as keeping the existing will point to 01-pihole.conf which does not work until pi-hole is installed)
# Ubiquiti switched the resolver to systemd-resolved which reserves the port 53
# dnsmasq install will fail to start dnsmasq so lets resolve that
sudo systemctl stop systemd-resolved
sudo systemctl disable systemd-resolved
sudo systemctl start dnsmasq
#Install pi-hole
cd /tmp
wget -O basic-install.sh https://install.pi-hole.net
#Install optional dependencies
#apt-get install man
#Install required dependencies
apt-get install whiptail
apt-get install dhcpcd5
apt-get install git
apt-get install dnsutils
apt-get install lsof
apt-get install unzip
apt-get install idn2
#downgrade libsqlite3 to support sqlite3
apt-get install libsqlite3-0=3.16.2-5+deb9u1
apt-get install sqlite3
apt-get install resolvconf
apt-get install lighttpd
apt-get install php-common
apt-get install php-cgi
apt-get install php-sqlite3
sudo apt-get update
sudo apt-get upgrade
sudo apt-get full-upgrade
sudo apt-get –purge autoremove
# Install PI-HOLE now
bash basic-install.sh
if above command fail, run this;
curl -sSL https://install.pi-hole.net | bash
if above command to install PI-Hole fails on OS check, run this;
curl -sSL https://install.pi-hole.net | PIHOLE_SKIP_OS_CHECK=true sudo -E bash
#Reconfigure lighttpd port (for example 8080)
nano /etc/lighttpd/lighttpd.conf
#Restart lighttpd
/etc/init.d/lighttpd restart
#Change the pi-hole random password to your liking
pihole -a -p
Navigate to the URL and it should be up and running.
If the pi-hole is not exposed to internet and properly firewalled, you can choose one of these options;
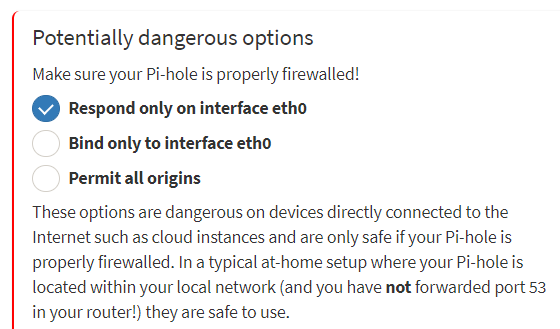
This will help you to see all of your clients (wired/wireless). Also you wouldn’t see “DNS request timed out” when do a nslookup, for example
nslookup google.com
If you want to see LED scrolling on Cloud Key, install one of Unifi App for example Protect or Doorbell. I have no issues with Pi-Hole with the App.
Make these configuration changes after PI-Hole installations;
nano /etc/pihole/pihole-FTL.conf
PRIVACYLEVEL=0
IGNORE_LOCALHOST=yes
MAXLOGAGE=24.0
MAXDBDAYS=180Restart pihole-FTL to make the changes effective
sudo service pihole-FTL restart
To uninstall Pi-Hole, run this command;
sudo pihole uninstallAfter uninstalling, run these commands;
sudo systemctl enable systemd-resolved
sudo systemctl start systemd-resolved
Some frequent Pi-hole/Linux commands are;
# Pi-Hole related
# Command to see if the database exists:
stat /etc/pihole/pihole-FTL.db
#If it does, then run these commands:
sudo service pihole-FTL stop
sudo rm /etc/pihole/pihole-FTL.db
sudo service pihole-FTL start
# Pi-Hole stores its 24 hour log here:
/var/log/pihole.log
# debian related
dpkg --list
systemctl status lighttpd
systemctl start lighttpd
systemctl stop lighttpd
systemctl restart lighttpd
# List of ports that are in use
sudo lsof -l -P -n | grep LISTEN
Your Pi-Hole is up and running. It’s time to decide if you want Pi-hole as All-Around DNS Solution? If yes, then follow these instructions on Pi-Hole web site or this site.
You want to change database location, follow this link.
If Cloud key updated and Pi-hole does not work, follow this link.
Resources
https://help.ui.com/hc/en-us/articles/220334168-UniFi-Cloud-Key-Emergency-Recovery-UI