To secure your web app make sure you have setup HTTPS only and client certificate required.
To further restrict access, you can setup IP address-based rule.
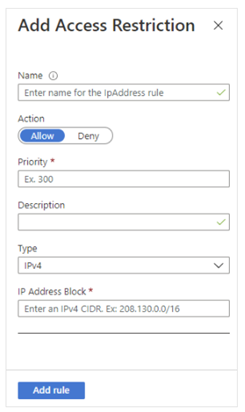
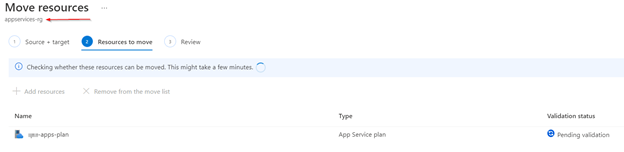
To add an access restriction rule to your app, select Networking under settings and click on Configure Access Restrictions. On the Access Restrictions pane, select Add rule. After you add a rule, it becomes effective immediately.
Rules are enforced in priority order, starting from the lowest number in the Priority column. An implicit deny all is in effect after you add even a single rule.
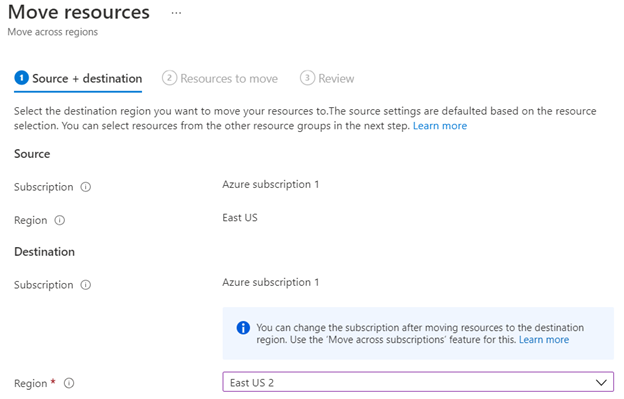
On the Add Access Restriction pane, when you create a rule, do the following:
- Under Action, select either Allow or Deny.
- Optionally, enter a name and description of the rule.
- In the Priority box, enter a priority value.
- In the Type drop-down list, select the type of rule.
The different types of rules are described in the following sections.
Note
- There is a limit of 512 access restriction rules. If you require more than 512 access restriction rules, we suggest that you consider installing a standalone security product, such as Azure Front Door, Azure App Gateway, or an alternative WAF.
Set an IP address-based rule
Follow the procedure as outlined in the preceding section, but with the following addition:
- For step 4, in the Type drop-down list, select IPv4 or IPv6.
Specify the IP Address Block in Classless Inter-Domain Routing (CIDR) notation for both the IPv4 and IPv6 addresses. To specify an address, you can use something like 1.2.3.4/32, where the first four octets represent your IP address and /32 is the mask. The IPv4 CIDR notation for all addresses is 0.0.0.0/0. To learn more about CIDR notation, see Classless Inter-Domain Routing.
Azure DevOps required to deploy build to App Services and we need to allow these services for this use case. Microsoft has introduced an AzureDevOps service tag for it but as of this writing the tag is not working. The work around is to open app to selected geography where Azure DevOps is running. In my case, they are running in EASTUS. I am going to add this rule to allow Azure DevOps to works with Azure App Service;
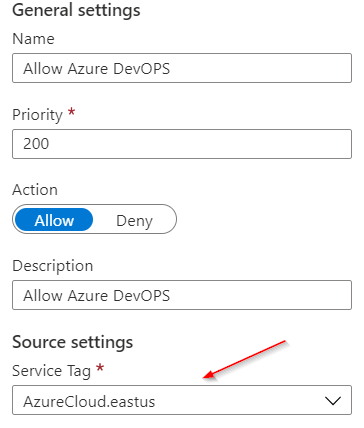
This will open up App to the whole EastUS region but still is better than opening it up to the whole world.
As of this writing Azure DevOps Service tag is not supported for hosted agents. AzureDevOps tag does not cover Microsoft Hosted Agents IP range, which makes the use case for using it in Azure App Service limited. The only relevant use case is, if a custom web hook is hosted on App Services.
Azure DevOps IP address and domain URLs can be used and Azure Virtual machine scale set agents to shrink the possible IP range. Refer to following links for further info;
DevOps Inbound connections: Allowed address lists and network connections – Azure DevOps | Microsoft Docs
Scale set agents: Azure virtual machine scale set agents – Azure Pipelines | Microsoft Docs
SET AN IP ADDRESS-BASED RULE USING POWERSHELL
Add-AzWebAppAccessRestrictionRule -ResourceGroupName “appservice-rg” -WebAppName “simse” -Name IpRule -Priority 200 -Action Allow -IpAddress 100.15.181.143/32
Resource
https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions
https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions