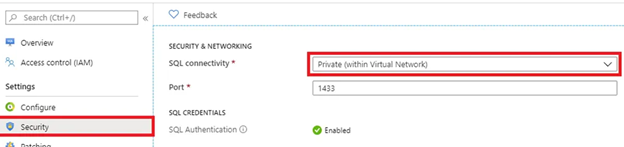
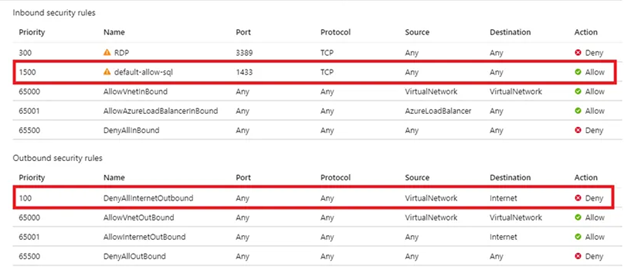
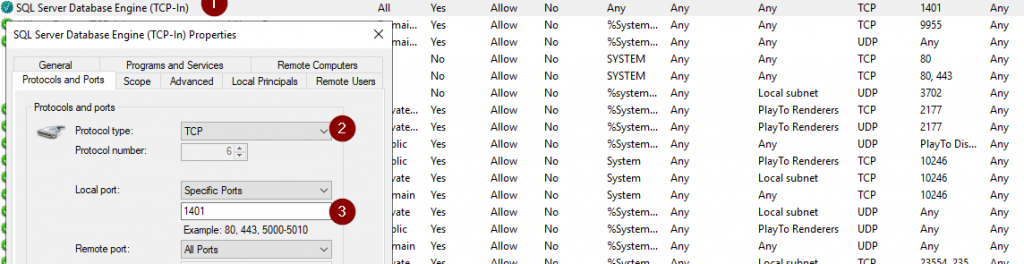
VLANs had me confused and running in circles for a while when I was first setting them up too. My understanding of things may not be entirely correct or the “right” way of doing things, but it worked for me. I don’t have experience setting up VLANS in the Unraid interface, but my experience getting VLANs working may help you notice something you overlooked.
I believe you need switches and a router that support VLANs, also known as 802.1q. The switches certainly need support for VLANs and I believe the router may need it to route traffic between VLANs (e.g. from VLAN 4 to VLAN 9), perform network management things like DHCP, and access the Internet. Many consumers routers and basic unmanaged switches don’t support VLANs. Third-party firmware like OpenWRT may be able to add VLAN support to consumer routers. I’m not sure what a “smart unmanaged” switch is, but if it doesn’t have some sort of an interface, be it Web, software, serial/RS-232, or ssh/telnet based, it isn’t smart enough to support VLANs; all VLAN configuration is performed on the device itself via some sort of interface. Check the spec sheets on your gear.
I ended up using Netgear GS108Tv2 and GSS116E switches with a pfSense router running on a Dell 780 SFF PC with a I350-T2V2 network adapter. The fancy network adapter isn’t required. The 116E switch has basic “port-based” configuration, but the 108T doesn’t, so I used “advanced” VLAN configurations.
The first major concept to understand is that network traffic doesn’t have VLAN tags until you turn on VLAN support. Traffic on VLANs has extra data added to it, (the 802.1q header), that requires routers and switches to understand VLAN-formatted traffic.
The second major concept to understand is the Port VLAN ID (PVID). It appears to be the default VLAN ID for a port.
The third major concept to understand is VLAN membership. A port is a member of a VLAN if it’s marked as “tagged” or “untagged” on a VLAN. Most devices, e.g. PCs, game consoles, iPads, etc., don’t understand VLANs and so their traffic does not contain a VLAN tag; their traffic is “untagged” when entering the network. “Untagged” ports assign the PVID of the port to the traffic, giving it the VLAN information needed to move on a VLAN network; traffic inherits the VLAN ID from the port. My networked devices are all “untagged” on once VLAN, making them a member of a single VLAN.
“Tagged” ports appear to be designed to move traffic that is is already tagged. This could theoretically come from a device that understand VLANs or be traffic from an “untagged” port that had a tag added by the switch. Cisco uses a technology called “trunk” ports for passing traffic between switches and routers that Netgear doesn’t have. I use “tagged” ports to accomplish this task. My “trunk” ports are tagged in all VLANs, making them a member of all VLANs and allowing them to communicate with all VLANs while passing traffic between switches and routers.
All my networked device are on “untagged” ports but they they inherit a VLAN ID from the port; they become “tagged” by the switch rather than the original device. Once the traffic from a device is tagged by the switch, it can communicate with any device on the same VLAN. Communicating with devices on a different network switch or communicating with devices on the Internet requires the “trunk” ports that are tagged in multiple VLANs.
I set up VLAN 1, 4, and 9; 1 is used for network management, 4 is for my PCs and such, 9 for my Unraid server.
My only experience is with the Netgear stuff, so some of the terminology may be different with other brands.
So if Port 1 connects the switch to the router, Port 1 would bet marked as tagged on VLAN 1, 4, and 9 in my setup, making it a member of VLAN 1, 4, and 9; this makes it something like a “trunk” port between the switch and router and allows all the traffic can get upstream to the router as needed. My “trunk” ports also got a PVID of 1; they always tagged traffic, so the PVID may not matter.
If Port 2 is connected to my desktop PC, it would get a PVID of 4 and is untagged on VLAN 4 only. This allows the port to only communicate with other devices on VLAN 4.
If Port 3 is connected to my laptop, it would get a PVID of 4 and is untagged on VLAN 4 only. This allows the port to only communicate with other devices on VLAN 4.
If Port 4 is connected to my Unraid server, it would get a PVID of 9 and is untagged on VLAN 9 only. This allows the port to only communicate with other devices on VLAN 9.
The fourth major concept is inter-VLAN routing. My PC and laptop in the example above can talk to each other because they’re both on VLAN 4 and can talk to the router via the trunk on port 1. The Unraid server can talk to the router. However, members of VLAN 4 can’t talk to members of VLAN 9. I remedied this with firewall rules in the router. These rules allow me to control which devices (IP addresses) and services (ports) on VLAN 4 can communicate with which devices and services on VLAN 9. I believe this is a reason why the router needs VLAN support – you’re routing between VLAN networks (e.g. 192.168.4.100 to 192.168.9.10). The router may also need to understand the VLAN-formatted packets so it can strip off the VLAN formatting before forwarding it to the Internet.
So I added firewall rules in pfSense to allow my PC and laptop to access the Unraid web UI, ssh, file sharing ports, Plex ports, etc. of my Unraid server.
See more here